Four types of fake key attacks. Each diagram represents Alice (left)
4.9
(245)
Write Review
More
$ 22.00
In stock
Description

False or misleading statements by Donald Trump - Wikipedia

System overview of OrgAn, where a set of non-interacting users

Breaking the Bluetooth Pairing – The Fixed Coordinate Invalid Curve Attack
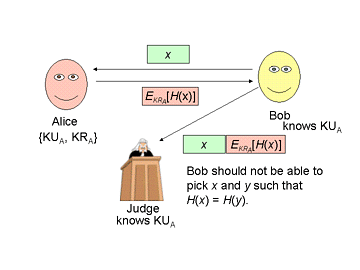
CS551: Problem Set 3: Public-Key Cryptosystems

Dignity Debased: Forced Anal Examinations in Homosexuality Prosecutions

PDF) Automatic Detection of Fake Key Attacks in Secure Messaging
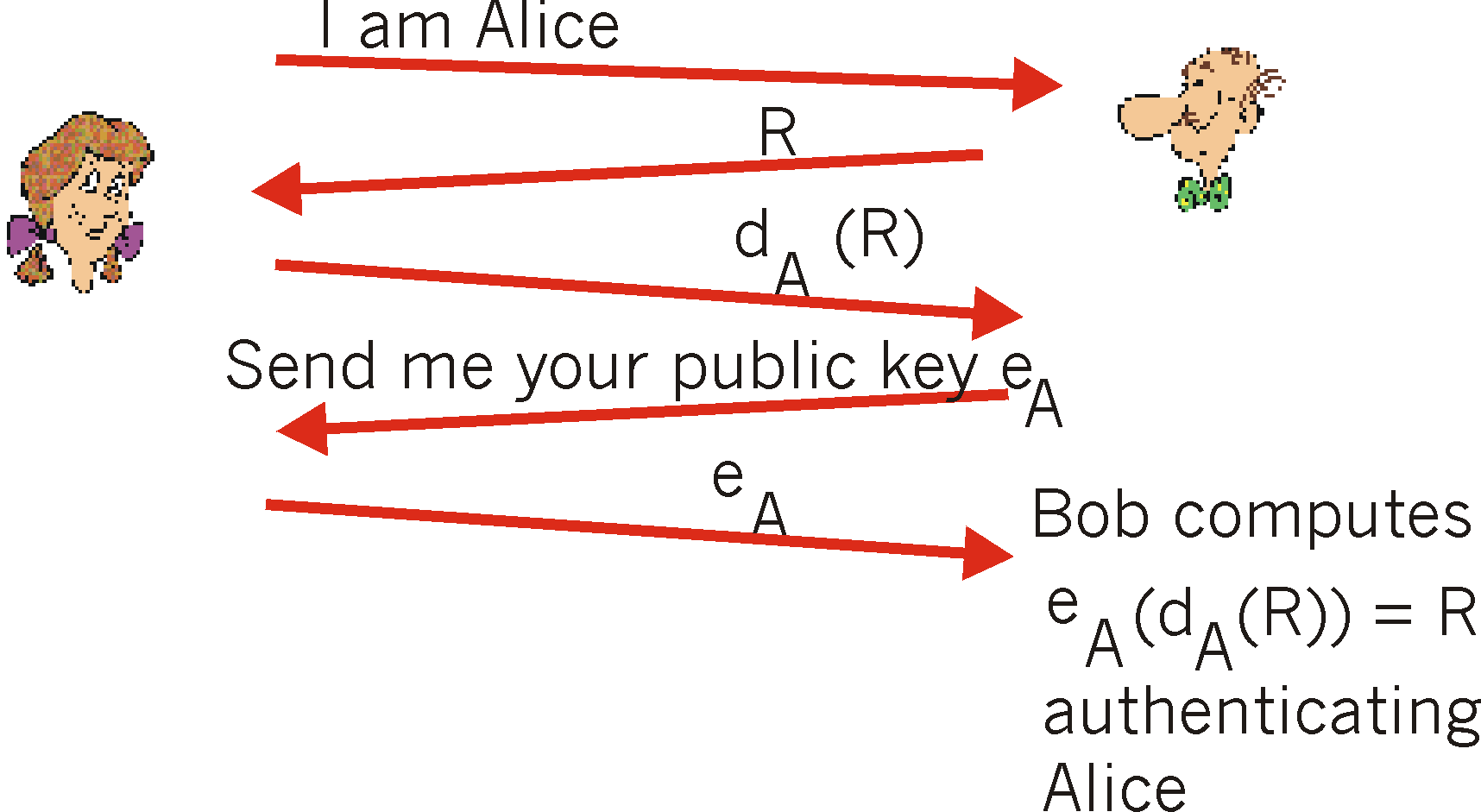
Authentication
Identity Security

Four types of fake key attacks. Each diagram represents Alice (left)
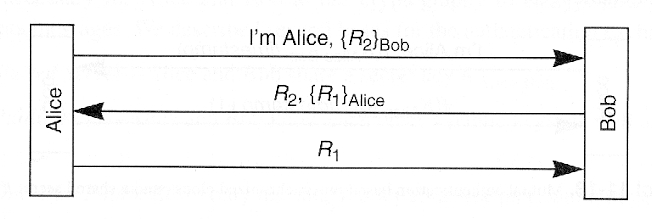
Chapter 11

15.1 Asymmetric Encryption Explained :: Chapter 15. Asymmetric Encryption :: Part III: .NET Cryptography :: .NET Programming security :: Programming
Related products
You may also like









