Threat Hunting - Simplifying The Beacon Analysis Process - Active
In part one of this two-part series, I described what is involved with performing a beacon analysis and why it is so important […]
Threat Hunting - Simplifying The Beacon Analysis Process - Active Countermeasures
ThreatHuntingJupyterNotebooks/BD-Threat Hunting for Malware Beacons.ipynb at main · BinaryDefense/ThreatHuntingJupyterNotebooks · GitHub

The Automotive Threat Modeling Template, NCC Group Research Blog

Threat Hunting: Process, Methodologies, Tools And Tips

The art and science behind Microsoft threat hunting: Part 2

Threat Simulator - Active Countermeasures
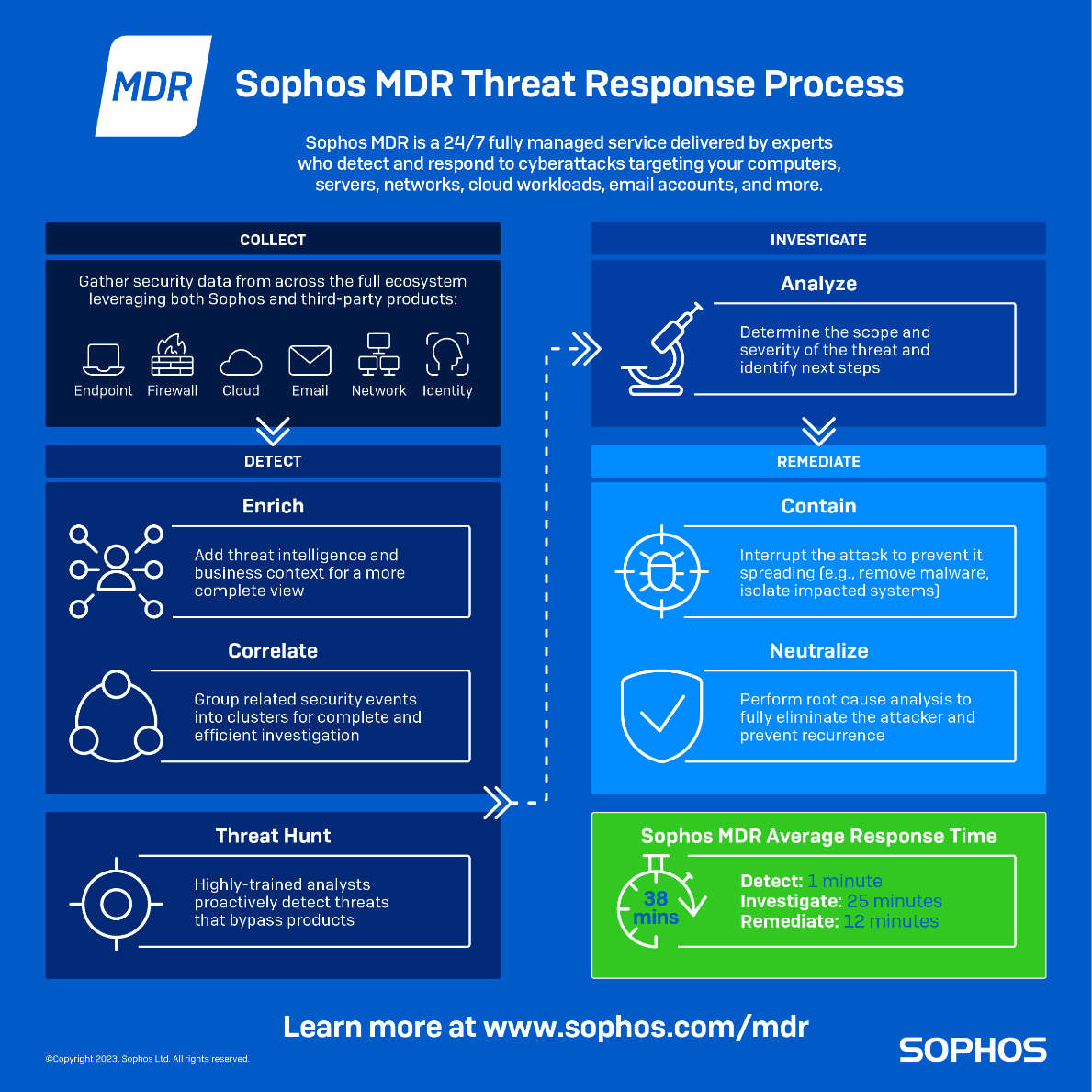
What is Threat Hunting? Threat Hunting Explained
Webcasts - Active Countermeasures

How effective is your cyber security threat hunting programme? - PwC UK
Patch Your WSO2: CVE-2022-29464 Exploited to Install Linux-Compatible Cobalt Strike Beacons, Other Malware
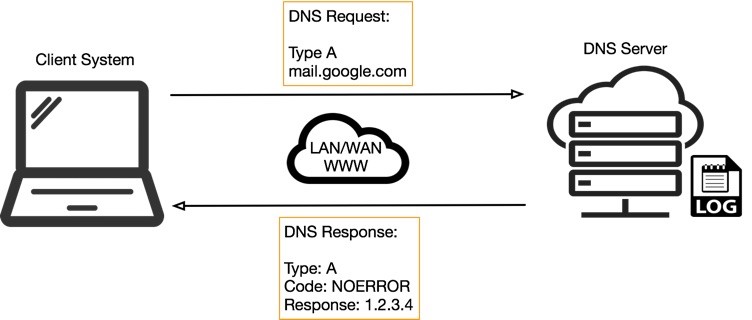
DNS Tunneling: how DNS can be (ab)used by malicious actors
Threat Hunting Series: The Threat Hunting Process, by Kostas
Identifying beaconing malware using Elastic — Elastic Security Labs

Threat Hunting Architecture

Threat Simulator - Active Countermeasures






